
The shift towards hybrid work models has expanded the perimeters of work, adding to the burden on IT teams as they fight to stay resilient in the face of increased attack surfaces. All it takes for an invasion into an enterprise’s IT infrastructure is one compromised identity.
So, what are enterprise identities?
These are the usernames, passwords, networks, endpoints, applications, etc., that act as gateways to business-sensitive information. Securing enterprise identities requires a well-defined identity and access management (IAM) strategy.
What is an IAM strategy?
An IAM strategy works by providing the right access to the right people by authenticating and authorizing their identity. Devising an ideal and comprehensive IAM strategy is critical for enterprises to thwart attacks and maintain a resilient infrastructure.
The need for IAM
Efficient management of identities through a proper IAM strategy ensures the establishment of secure user access workflows in organizations. IAM offers a seamless experience for end users and reduces the burden on IT teams. It also serves as a basis for efficient root cause analysis in case of data breaches that commonly occur due to compromised credentials and allows for a faster mitigation process.
How does IAM work?
When it comes to data access, IAM takes a two-pronged approach: authentication and authorization.
Authentication is the process of verifying user identity. To be precise, it is the mode of entry into a pool of data with the help of credentials. There are different ways to authenticate users:
Authorization is the process of validating and governing user access. This is usually done through identity governance and administration (IGA) and privileged access management (PAM), which function as integrated access management units.
| AUTHENTICATION | AUTHORIZATION |
| A point of entry for any user to access a resource. | Validation process that determines who has access to what. |
| A preliminary step to access corporate endpoints such as servers, applications, databases, and so on. | Based on user roles, the provisioning of privileges may vary. |
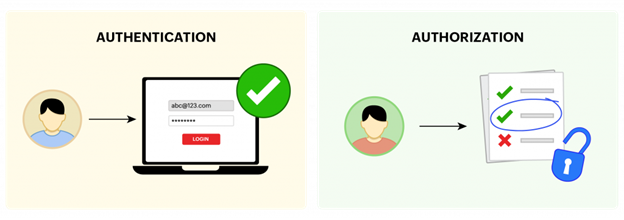
For example, during an online purchase, a user’s access to the payment gateway is authenticated by verifying the 16-digit card number and the card verification value (CVV). Once these details are processed, the validity of the card and availability of funds are checked, and authorized access is granted for the completion of payment.
Striking a proper balance between these processes maintains the confidentiality of data, thereby curbing external intervention, or misuse, of user credentials by malicious insiders.
Introducing IGA and PAM
IAM typically consists of a predetermined set of policies, best practices, and workflows to regulate user access activities across an organization. At its core, IAM consists of two modules: IGA and PAM.
IGA is a discipline of IAM that provides a centralized framework for enterprise identity management. IGA typically involves creating user accounts, provisioning, regulating, and auditing their accesses. IGA ensures effective implementation of IAM and also caters to the requisites of audit and compliance.
PAM is a discipline of IAM that enables the secure management of privileged identities. Since escalated access cannot be provided to every user, PAM solutions function by offering the least privilege and Zero Trust administrative access to its users, entirely based on merit.
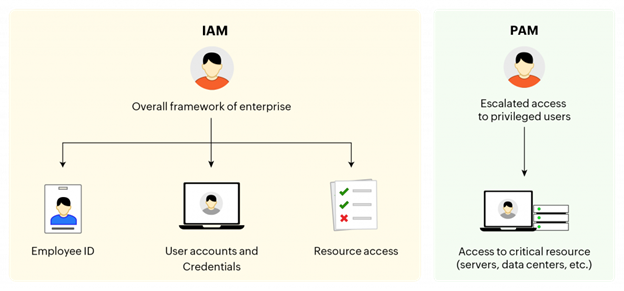
For example, the onboarding process of an employee comes under the purview of an IGA framework. This includes allocating an employee ID, mapping endpoints, establishing user accounts and credentials, and granting access to corporate resources.
However, if the employee’s role requires exclusive access to critical IT endpoints such as servers, databases, data centers, and network devices, among others, PAM comes into play. PAM caters to users with critical access requirements and includes granular access control mechanisms to ensure only administrative users have access to business-sensitive information.
Simply put, while IGA deals with overall access provisioning and governing across the organization, PAM deals with securing and governing administrative access to privileged identities.
Delving deeper into PAM
PAM is a cybersecurity strategy that aims at granting secure and escalated user access to privileged identities.
Privileged identities are being touted as a new currency; that is, they are the easiest modes of navigation into unlimited critical information of an enterprise. Service accounts, passwords, authentication tokens, and SSH keys are some examples of such identities.
A privileged user can either be a human or non-human user who has secure access to endpoints like databases, networks, cloud applications, and so on. As enterprises move towards more sensitive data, it is essential to restrict accessibility to maintain a secure environment.
How are privileged users granted access to such critical data? A set of digital entities like usernames, passwords, and other credentials become the gateway for safely accessing enterprise resources.
Managing privileged identities using PAM
Traditional methods of handling privileged identities have revolved around password vaults. However, with a rise in hybrid endpoints and cloud-based applications, organizations need to adopt the principle of least privilege, which narrows down the attack surface of critical data by granting role-based limited access to corporate resources.
With the scope of privileged access extending beyond IT teams, hassle-free management of identities demands strategies that go beyond conventional credential vaulting.
How can PAM make a difference?
The need for PAM: Business use cases
To understand the scope of PAM in an IT environment, let us consider the following use cases.
Scenario 1: Developers share their code snippets on developer forums while being oblivious to any sensitive information, such as authentication tokens, private keys, and so on, lurking in those scripts. This can expose critical data to anybody with malicious intent.
Solution: IT teams deploying a PAM solution initiate an automated password reset process that generates a new password and protects critical information from being publicly accessible. Thus, any attempt to reveal the credentials, knowingly or unknowingly, ends in vain, as they are no longer valid. The corporate endpoints remain intact.
Scenario 2: When employees leave an organization, IT teams need to ensure that their access privileges are rescinded or transferred. Standing privileges, which are ‘always on’ and persistently available with no active user, can increase the risk of cyber threats. These are low-hanging fruits for attackers, and their unlimited availability can expose critical enterprise data.
Solution: A PAM tool allows IT teams to ensure that the existing privileges are revoked and transferred to another privileged user. This prevents the exploitation of the ex-employee’s user credentials by malicious insiders.
Requisites of an ideal PAM program
An ideal PAM program must look after the lifecycle of privileged identities, and goes through the following stages:
Essentials for a PAM solution
The underlying principle of PAM is to stay ahead of cyber threats rather than mitigate invasions that have already taken a toll on the organization’s reputation. Considering these requisites under a single roof, an ideal PAM solution must:
Privilege identity abuse can result in major consequences for businesses, including loss of revenue and reputation. Investing in a PAM solution allows IT teams to manage and automate their privileged access routines, thereby complementing their PAM strategy. Additionally, PAM solutions offer real-time, actionable insights into privileged access activities to aid in the effective management and prevention of security incidents.